The file access method illustrated in the diagram above i...
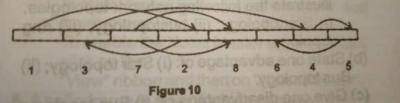
The file access method illustrated in the diagram above is called?
hashed access
indexed access
random access
sequential access
Correct answer is B
No explanation has been provided for this answer.
Similar Questions
Data to be processed by the microprocessor is temporarily stored in the? ...
The main difference between a laptop and a desktop is that, a laptop? ...
Use figure 4 to answer question 23 The basic problem with the flow chart is that it has ...
Use the MS-Excel table below to answer questions 48 to 50. A B C D 1 BOOKS S...
Computer files can be characterised by all but, ...
When a file or folder is deleted, it goes to the? ...
Computer ethics are important because they? ...
The shortcut key for the open dialog box in MS Word is ? ...