Computer Science Questions and Answers
Challenge your competence level in computers, computing, algorithms, hardware and software with these Computer science questions and answers.

Challenge your competence level in computers, computing, algorithms, hardware and software with these Computer science questions and answers.
Duplicating copyrighted electronic or digital content without the authors approval is considered?
felonious
ethical
treasonable
unethical
Correct answer is A
No explanation has been provided for this answer.
stored using a key
sorted in a particular order
stored as they come
stored in any storage media
Correct answer is C
No explanation has been provided for this answer.
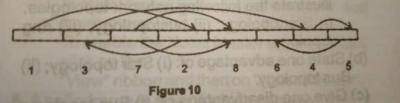
The file access method illustrated in the diagram above is called?
hashed access
indexed access
random access
sequential access
Correct answer is B
No explanation has been provided for this answer.
sorted using index
sorted in a particular order
stored as they come
stored in any storage media
Correct answer is B
No explanation has been provided for this answer.
The octal fraction 0.65 converts to binary as
0.110011
0.110101
101101
101101
Correct answer is B
No explanation has been provided for this answer.